I recently was working with a group of computers running Windows 7 Enterprise (32 bit version) that were having issues with complaining that “This copy of Windows is not genuine”. The really weird part about it is that in most cases the product was activated! How can it activate if it isn’t genuine? I have no idea!
First, though, let me explain what this article is not about. This is not an article on how to hack Microsoft Genuine Advantage in order to run an illegal copy of Windows. This is not an article about how to activate it with an illegal product key. It is not an article on giving out product keys, and I will gladly block IP addresses for anyone who asks for one. However, if you truly have licenses for all copies of Windows, and if you’re running Enterprise you should know, and you know they were installed using a genuine Microsoft Windows install, then please read on.
Most of the “fixes” on the web tell you to run the slmgr command, but that won’t work in this case because it is supposedly activated. It still will not pass the Windows Genuine Advantage test.
I have found that in every case, running the mgadiag tool indicates an error 0x8004FE21, and it tells you it fails because the following files have been “tampered” with:
Tampered File: %systemroot%\system32\sppobjs.dll
Tampered File: %systemroot%\system32\sppc.dll
Tampered File: %systemroot%\system32\sppcext.dll
Tampered File: %systemroot%\system32\sppwinob.dll
Tampered File: %systemroot%\system32\slc.dll
Tampered File: %systemroot%\system32\slcext.dll
Tampered File: %systemroot%\system32\sppuinotify.dll
Tampered File: %systemroot%\system32\slui.exe
Tampered File: %systemroot%\system32\sppcomapi.dll
Tampered File: %systemroot%\system32\sppcommdlg.dll
Tampered File: %systemroot%\system32\sppsvc.exe
Tampered File: %systemroot%\system32\drivers\spsys.sys
Additionally, you may have some in the WAT subdirectory as well.
Yet, if you replace these files (you have to boot off a CD or stick to replace them, naturally), it will still fail.
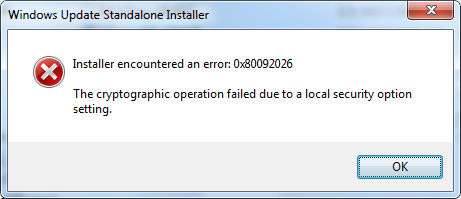
Worse, you cannot run the System Update Readiness test, CheckSUR, as it will not install. In fact, you really cannot install almost anything that would fix this issue, as you get an error 0x80092026, “The cryptographic operation failed due to a local security option setting.”
At the base problem, it would appear that Windows updates got installed out of order for some reason, and that caused a cascade of failures. In particular, I eventually found out that the Windows Update agent itself was not up-to-date.
The plan of attack, then, is to solve the cryptographic error, point Windows Update to the Microsoft servers instead of the enterprise Windows Server Update Server (WSUS), install the latest update agent and then let her rip on any and all missing updates (one was behind by 300, actually).
As a precaution, you might in addition want to run chkdsk before starting any of this at all, and afterwards you might want to run CheckSUR. This will ensure that no disk issues prevent the system from updating and any remaining issues get resolved.
The first two steps, solve the cryptographic 0x80092026 error and point the workstation to the Microsoft servers, involve changes to the registry. I will supply what goes into the .reg files, but if you know your way around the registry you can also do this by hand.
I call this one cryptographic_0x80092026_error.reg:
Windows Registry Editor Version 5.00 [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing] "State"=dword:00023c00 [HKEY_USERS\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing] "State"=dword:00023c00 [HKEY_USERS\.DEFAULT \Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing] "State"=dword:00023c00
This next one I call BypassWindowsServerUpdateServer.reg:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU] "UseWUServer"=dword:00000000 "NoAUShutdownOption"=dword:00000001 "NoAutoUpdate"=dword:00000001
Save them with “.reg” extension, and you can double-click on them to add the information to the registry. Please note, however, that Windows by default turns off known file extensions, so you might have to save them as text files using notepad, save them onto the desktop and then rename them using these commands from the command line prompt:
cd Desktop ren cryptographic_0x80092026_error.txt cryptographic_0x80092026_error.reg ren BypassWindowsServerUpdateServer.txt BypassWindowsServerUpdateServer.reg exit
You can now double-click on these files, and they will enter the information into the registry.
Now you will be able to download and run the latest Windows Update agent. I recommend saving it into your Downloads folder and then running it. That way, if it still fails, you at least have a copy of it on your hard drive.
Assuming that worked, now you can run Windows Updates and catch up. Hopefully, you won’t have 300 updates, which takes about 4 hours to download and install.
I recommend running it in a GUI just to be sure whether or not any fail, but if you are automating this, you might want to look into using an MS supplied script WUA_SearchDownloadInstall.vbs at least for the initial round.
If you still have issues with WGA after the updates, I suggest checking out KB971033 from Microsoft. Then, run CheckSUR once again.